In the dynamic world of cybersecurity, vigilance is not just a virtue—it's a necessity. Recently, as CrowdStrike cause a major global outage, NCSC report that cybercriminals are siezing the opportunity to launch a wave of phishing attacks targeting its users. These attackers are like sharks sensing blood in the water, ready to pounce at the first sign of vulnerability.
Opportunistic phishing is akin to a pickpocket preying on a bustling crowd. These cybercriminals exploit significant events, such as network outages or security breaches, to craft convincing phishing emails designed to steal sensitive information. It's a classic case of using chaos to gain an upper hand, and this recent CrowdStrike fiasco is a perfect example of this insidious tactic.
CrowdStrike Outage and Phishing Attempts
In the wake of the CrowdStrike outage, phishing emails began flooding inboxes worldwide. These emails are masterclasses in manipulation, deftly combining urgency with a veneer of legitimacy. Let’s dissect three possible examples, starting with the most sinister of the lot.
Sample Phishing Email 1: Steps to Recover from Outage
Picture this: You’re an IT professional, your inbox pinging with alerts about the CrowdStrike outage. Amidst the flurry of messages, one email stands out. It's from the “CrowdStrike Security Team,” warning of critical system failures due to a software bug. The message is direct and urgent:

“Dear User,
...
To prevent further system damage and data loss, it is imperative that you follow the recovery instructions immediately. Click on the secure update link below to proceed. Failure to do so within the next 24 hours may result in irreversible damage.
Secure Update Link
...
Sincerely,
CrowdStrike Security Team"
The email is a textbook example of phishing elegance. Let’s break it down:
- Official Branding and Logos: The email uses the CrowdStrike logo and color scheme, making it look authentic at a glance.
- Urgent Language: Words like "imperative," "immediately," and "irreversible damage" trigger a sense of panic, urging the recipient to act without thinking.
- False Sense of Security: Providing a support contact (albeit fake) makes the email seem legitimate, lulling recipients into a false sense of security.
This email preys on the chaotic aftermath of the outage. It’s like a thief shouting “Fire!” in a crowded theater, knowing people will scramble without checking the source of the alarm.
Analyzing Phishing Tactics in Detail
To better defend against these attacks, we need to understand the psychology behind them. Phishing emails like the aforementioned one exploit three main tactics: urgency, authority, and fear.
-
Urgency:
- Cybercriminals rely on creating a pressing need to act, as urgency compromises the ability to think critically.
- In our phishing email, phrases like "act immediately" short-circuit the user’s usual caution.
-
Authority:
- Using logos and official-looking emails give an illusion of authority. Recipients are more likely to trust and act on instructions from what appears to be an authoritative source.
- By mimicking the official CrowdStrike communication style, attackers leverage the brand’s authority.
-
Fear:
- Fear is a powerful motivator. Here, the fear of system failure and data loss pushes recipients to follow the provided instructions.
- The phishing email exacerbates this fear, suggesting severe repercussions for inaction.
Sample Phishing Email 2: License Expiry Warning
Let’s briefly touch on another phishing example, which rides on the coattails of fear and urgency.

“Dear User,
...your CrowdStrike license is expiring soon. .. Failure to renew may increase the risk of encountering the severe BSOD issue and could leave your organization vulnerable to security threats.
...
Click here to renew your CrowdStrike license immediately ...
Regards,
CrowdStrike Support Team”
Again, this email dials up the fear factor—this time, around license expiry and potential system failures. With official guidance links and severe warnings, it’s designed to panic users into clicking without second thoughts. It’s equivalent to a door-to-door scammer claiming your utility bill is overdue, pressuring you to pay immediately to avoid disconnection.
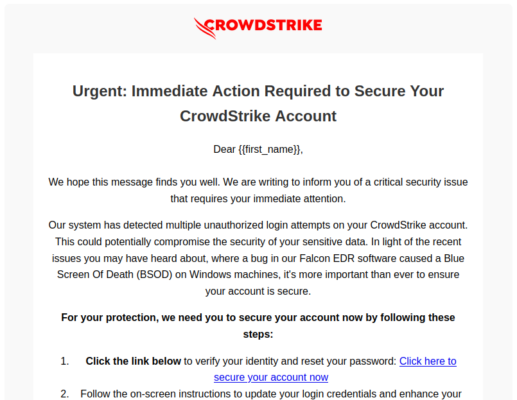
Sample Phishing Email 3: Unauthorized Login Attempts
Lastly, consider the third example:

“Dear User,
Our system has detected multiple unauthorized login attempts on your CrowdStrike account. ... In light of the recent issues you may have heard about ... Falcon EDR software bug caused a Blue Screen Of Death (BSOD) on windows machines, ...
Click here to secure your account now
...
Best,
CrowdStrike Security”
Here, the fear of unauthorized access is heightened by the ongoing software issues. Cybercriminals are banking on users being hyper-vigilant due to the outage, and this message plays right into that anxiety.
In all these examples, the common thread is the exploitation of human emotions—fear, urgency, and trust. These emails use vivid descriptions of potential dangers, creating vivid mental images that rush the recipient into hasty actions.
CrowdStrike’s recent outage has highlighted a recurring theme in cybersecurity: attackers are always ready to exploit uncertainties. By understanding the sophisticated tactics used in phishing emails, we can better prepare ourselves and our organizations to thwart such deceptive adversaries. Remember, a calm and discerning approach is your best defense—always verify before you click. Keep your guards up, maintain your vigilance, and make it a habit to question the authenticity of urgent requests in your inbox.
Stay secure, stay informed, and think before you click!